
There’s a text message that no lawyer or office manager wants to receive. The one that came to Cecile’s personal phone at 7:00 a.m. said simply,
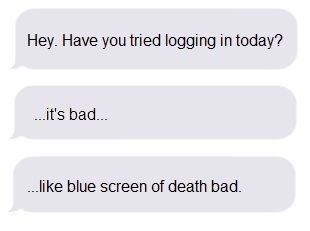
Cecile powered up her company laptop and it didn’t take long for her to realize the firm had been hacked. Every drive and file she attempted to access served up a blank screen. The criminals also left a note explaining that the files had been encrypted with RSA 2048-bit encryption that would be removed only after a ransom was paid. This was enough to effectively put every client file at risk and force a short-term shutdown of the firm.
It was time to activate the emergency response plan, the details of which were in a simple yellow folder in her drawer. It contained a list of all the firm’s employees, the key contact for their external tech support and a copy of the firm’s office insurance policy.
The first priority was informing the partners. She sent a note to both of them right away and made sure the phone ringer was on and waited for the calls.
What would you do next?
With luck and strict cybersecurity protocols in place, the scenario described above is one that you will never have to face. But cybercrime is on the rise and it pays to have an emergency response plan in place because the moment your files get locked by hackers, the risks to your firm’s reputation and financial position begin to mount quickly.

The firm’s response
In this case, Cecile’s firm had taken the advice of their insurance provider and purchased an office insurance policy that included cyber network security coverage. They knew it would provide the money needed to pay for the specialized tech support they would surely need.
David Camps, Vice President of Marketing and Client Experience at Lawyers Financial, refers to this kind of additional coverage as five policies in one because cyber network security insurance covers network security, privacy violation, cyber extortion, data incident recovery, and business interruption. “What clients are getting is five kinds of coverage in one plan and the flexibility to use the money as needed, up to a total of $250,000 each year,” he says. “It’s a very effective way to protect your business because criminals are likely to use a combination of attacks and you want the agility to respond in the best way for your firm,” he adds.

Restoring the practice
The firm was able to engage its technical support provider and get to work on restoring data by activating its insurance policy, using three of its five elements to cover costs incurred as a result of the attack.
Knowing that each component of their coverage would apply to specific steps in the restoration process, and they could spend up to $250,000 as needed, they were able to hire top-notch analysts capable of recovering the files. Here’s how three of the five coverage types became instrumental in getting the firm back to business.
| Type of coverage |
What it covers (up to a total of $250,000 a year using any combination of coverage) |
Activated? |
|---|---|---|
| Network security | Losses for the failure to protect a client's information. | NO. Luckily, no client information was stolen. |
| Privacy violation | Remediation of damages if a client files a privacy claim. | NO. Fortunately, no claims were filed. |
| Cyber extortion | Expenses incurred in the event of cyber extortion loss or cyber extortion threat. | YES. Because the cyberattack included extortion, costs were recouped. |
| Date incident recovery | The cost determining liability (if any) and ensuring a firm is compliant with privacy laws. | YES. Because external breach professionals were hired for data retrieval, analysis of the breach and mitigation. |
| Business interruption | The cost of continuing daily operations of the business. | YES. Because the cyberattack included extortion, costs were recouped. |
“The process of investigating this kind of crime takes time and money,” says Mr. Camps. “This isn’t like taking your car to the shop after a fender-bender. It takes a lot of effort to battle back from this kind of crime and that’s why you need to be protected.”
It’s impossible to predict when and if your firm will fall victim of a cyberattack. The best thing to do is plan for it with the right kind of insurance to protect your clients and your business.


